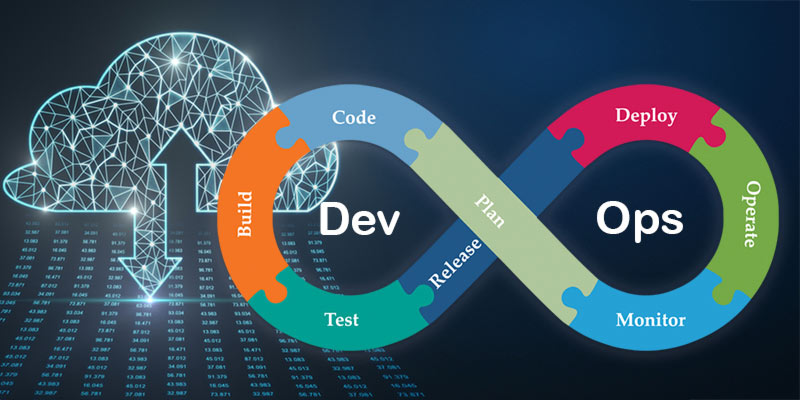
DevOps and DevSecOps are immature disciplines, but they've already established themselves as important practices for enterprise software development. The problems that these approaches aim to solve—security-related issues like buffer overflow, SQL injection attacks, and cross-site scripting (XSS)—are still relevant today, as attackers continue to innovate new ways of exploiting vulnerabilities in your software. By combining automation and AI, the shift from DevOps to DevSecOps will redefine software development in 2022. If you're not using DevOps or DevSecOps services strategies yet in your organization's IT environment, it may be time to rethink what works best for your team's unique needs.
Why You Might Be Failing at DevSecOps
DevSecOps is a new concept that has been around for less than 10 years. It’s still evolving, and it's important to stay on top of the latest developments in this space. It may seem like DevSecOps is a simple concept—you have code written by developers, who can then use that code to create software solutions for your business. But there are many layers between where your developers write code and where you deploy it into production (or even test environments).
The most obvious layer is security testing: how do you know that what you wrote works as expected when it gets delivered? How do you verify that no one got access to sensitive data or stole confidential information? There are also some other important considerations: who will be responsible for maintaining the infrastructure required by these applications? Who will monitor performance metrics such as response times or server load levels so that problems can be identified before they cause significant harm?
Perimeter Protection is Useless Against Modern Cyberattacks
The perimeter is dead, long live the application-aware firewall. The idea of a security boundary has been replaced by an application-aware firewall that controls traffic within your network and prevents data breaches from happening in the first place. This can include using deception technology to make it appear as if a malicious actor was never present on your network at all—or even encrypting all traffic going over public channels like Telnet or SSH so that no one can break through in plain sight (even though you know they're there).
Focusing on Vulnerabilities Won't Make You Secure
The first thing to understand is that vulnerabilities are just one part of the security puzzle. They're not the problem; they're symptoms of the problem. Vulnerabilities are not a solution in themselves, and they shouldn't be treated as such by your organization either—they're just one piece of an overall strategy for protecting data and systems from hackers and other bad actors who want them for their benefit. But without any knowledge or understanding of why you need to protect your organization's resources, it can seem like focusing on vulnerabilities will solve all your problems (and it might). So if you're looking at all these things as being equal parts, then why wouldn't you go after them all at once?
But here's where we run into another pitfall: You might feel like if you fix one vulnerability then everything else will be taken care of automatically—but this isn't true! If there were only two ways out there for hackers, then maybe but today there are so many options available partly because we've made mistakes like these over time...
Orchestration is the Key to Efficiency
The key to efficiency is orchestration. Orchestration is the coordination of multiple tasks and processes, often across different systems or applications. It can be used to ensure that all parts of your DevSecOps program are working in concert with each other, which reduces waste and improves performance.
DevSecOps uses several different tools for orchestrating tasks like:
- Continuous integration (CI) platforms like Jenkins or Travis CI
- Automation scripts that run on each commit to your source code repository (such as Grunt)
Failing to integrate the DevOps process into application development is leading organizations to the same old mistakes.
DevOps is a new way of working. It’s not a tool or a process, but rather an attitude and mindset that can be applied across all phases of your software development lifecycle (SDLC). It’s about collaboration, automation, and culture change - all wrapped up in one neat package! The DevOps process was developed by Amazon in 2012 as part of their move toward continuous delivery (CD) – where code is written in such a way that it can be released quickly without waiting for testing or approval from management. In addition to CD practices like automated deployments and test-driven development (TDD), you should also have separate teams responsible for each step along your SDLC: planning/architecture; coding; testing; quality assurance & security compliance testing, etc...
DevOps and its security cousin, DevSecOps, have matured beyond their infancy and established themselves as important practices in enterprise software development.
DevOps and DevSecOps are important practices in enterprise software development. Applying DevSecOps at scale is a significant challenge that requires an organizational culture change across the entire organization: from senior leaders to developers and security teams alike need to embrace this new way of doing things if they want their organizations' digital supply chains (DSC) processes to succeed.
How to Move DevSecOps Forward
DevSecOps is a broad term that encompasses a lot of different practices. It's not something you can buy or implement, but rather an approach to building secure software systems.
DevSecOps isn't just one thing: it's an attitude, mindset, and set of tools that help developers and testers work more closely together to build quality products faster while ensuring that security requirements are met at every stage in the development process.
It also involves collaboration between developers and security professionals who are responsible for implementing best practices when it comes time to build your product—and keeping them on track as they do so!
The Importance of Integration
Integration is the key to DevSecOps. Whether you're talking about security or development, integration on both sides of the equation is crucial for success. When it comes to DevSecOps, however, there's one key challenge: security must be an active participant from day one of a project's development cycle if you want any chance at all of having an effective DevSecOps practice in place.
Security should have a place at all levels of your application lifecycle—from initial requirements gathering through deployment and operation—and not just during deployments or post-deployment operations when things go wrong (which they often do). Security has always been important but now more than ever before because modern applications are so complex that they require constant monitoring and optimization by experts who know what needs fixing right away instead of waiting until after deployment or discovery issues arise later down the road
It's Time to Shake Things Up in Your Organization and Get the Security Team to Start Working Differently
Security teams need to work with developers to build security into the application development process. The speed and agility of cloud applications require a new way of thinking about security—digital transformation requires a new approach to security. This is not a code problem; it's a mindset problem!
Enterprises need to stop treating security as an afterthought: We've been doing this for so long that we've forgotten how good it feels when you're able to build something quickly, but still have your systems secure enough that they won't let anyone else steal or attack your business' data (or disrupt operations).
Removing security teams from the development process does little to improve productivity overall. The reason for this is that DevSecOps teams must be involved in every step of the process, including:
- Security testing and testing automation
- Deployment management and automation
- Operations monitoring
An obsession with speed is part of the reason for the lack of security in many applications and networks today.
Speed is important, but security should not be sacrificed for it. You can’t have your cake and eat it too—you must make sure that your security practices are not just fast, but also secure. Speed should never come at the expense of quality or reliability. Security must be fast because no one wants to wait five minutes for their coffee in the morning or ten minutes for their lunch break if there is an attack happening!
Conclusion
Security has always been a challenge in DevOps teams due to many factors like rapid changes in technology, short development cycles, and the lack of resources required to properly manage both these problems simultaneously (DevSecOps). Improvement starts by understanding why this practice is falling short in many organizations today and then developing new approaches to address those shortcomings. Start by understanding why this practice is falling short in many organizations today, and then developing new approaches to address those shortcomings.
The first step is to understand that DevSecOps isn't just about secure code—it's about making sure everyone on your team understands the importance of security and how they should approach it for their applications. For this practice to succeed, everyone needs buy-in from both ends: developers need to embrace practices such as automated testing; security teams need support from developers so they can focus on their primary role (protecting assets).
This can be achieved through training sessions or mentorship programs where individuals are paired up with each other or working groups within an organization where they share knowledge and expertise across teams' goals of improving efficiency while also ensuring compliance standards are met across all systems being developed within a given organization to thrive in the modern DevOps and DevSecOps world, you need to understand the challenges that are emerging, how they relate to your current practices, and what steps can be taken to improve them. SSE is a great example of this: it’s designed with both security and efficiency in mind so that developers can focus on building applications rather than worrying about how they will function once deployed.